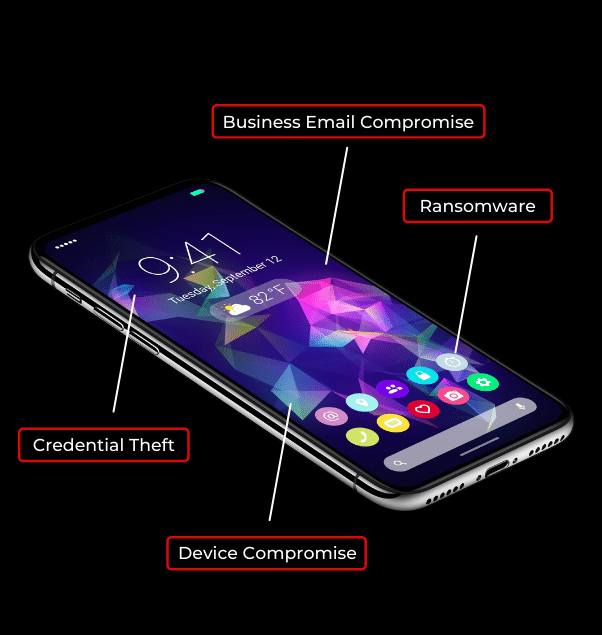
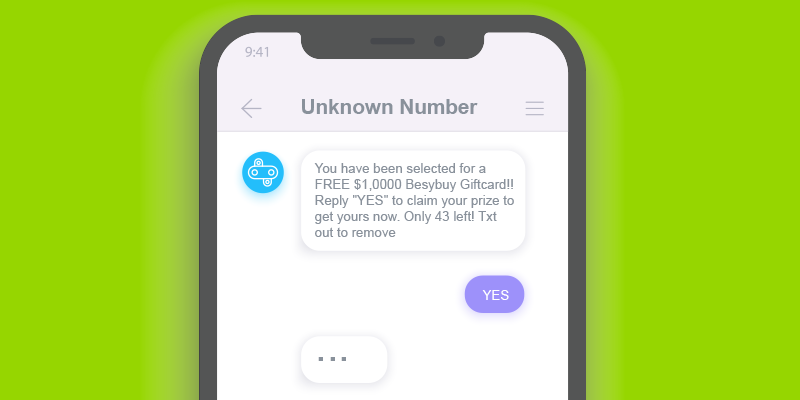
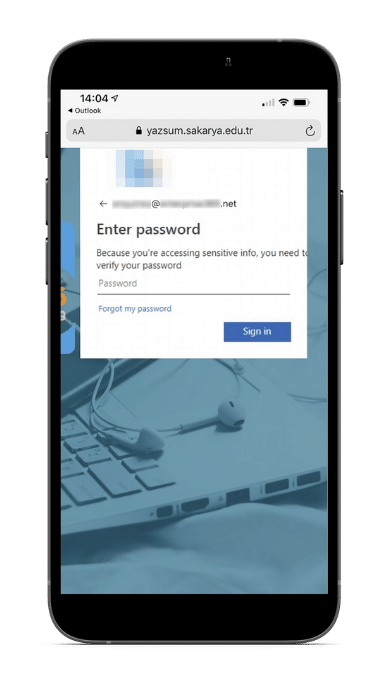
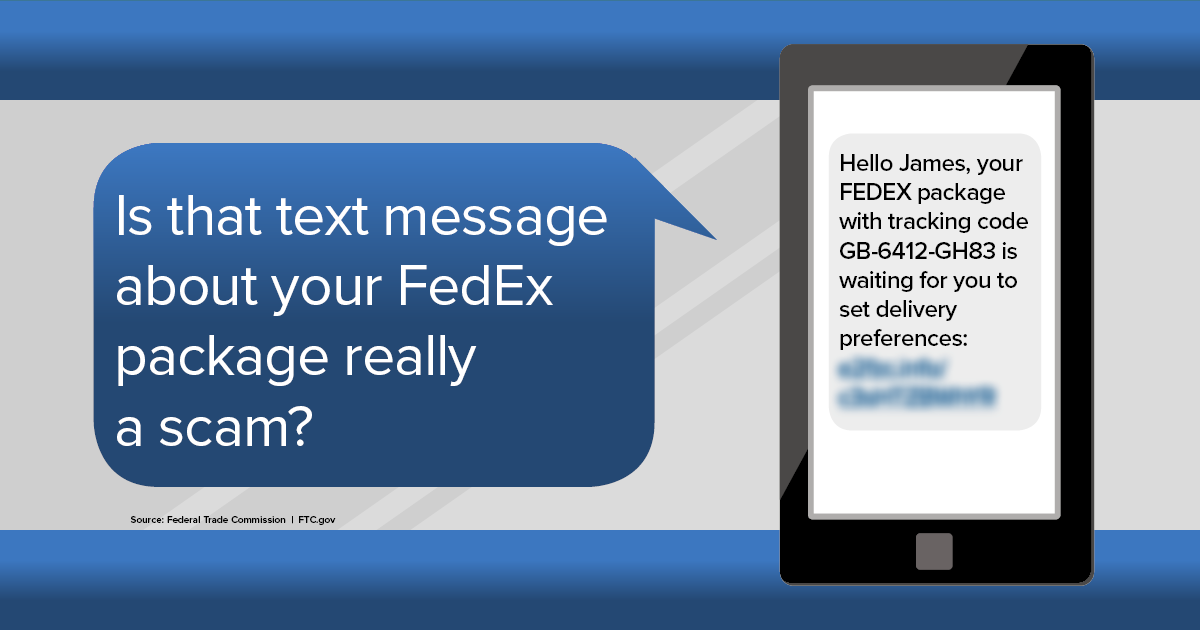
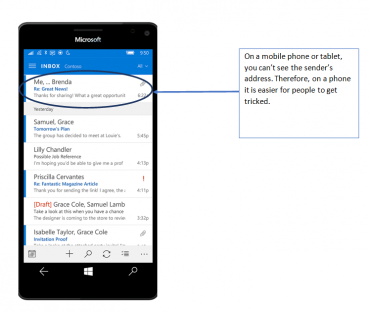
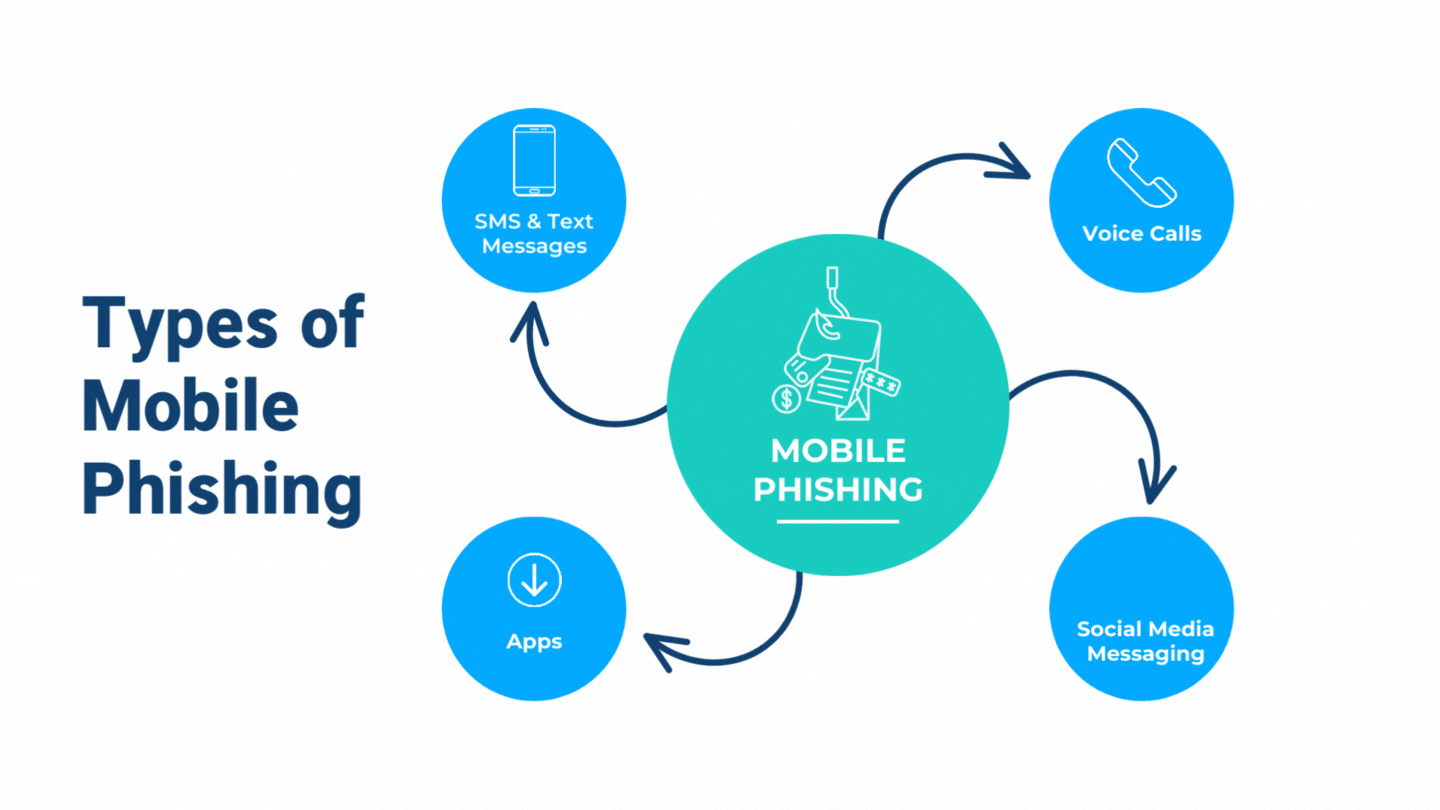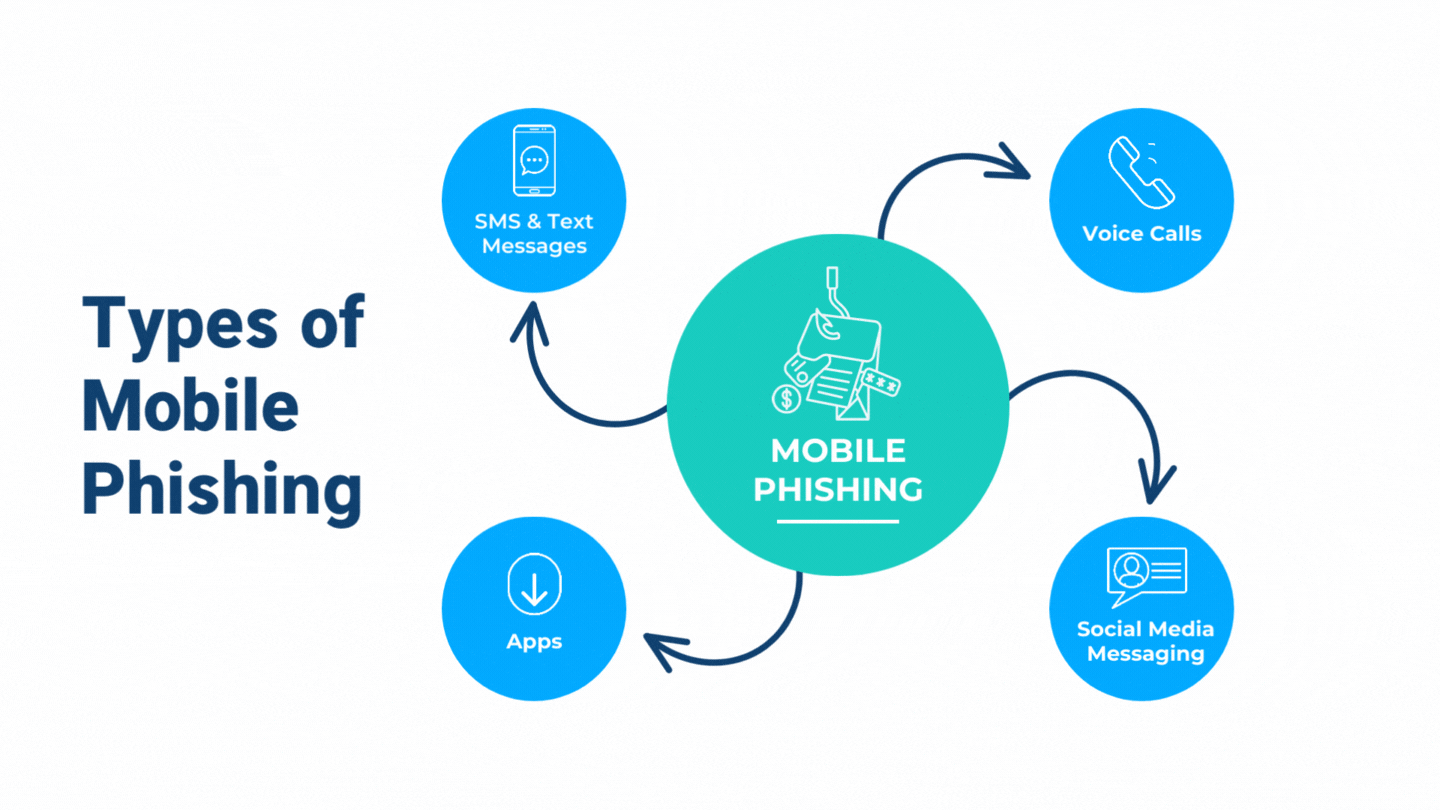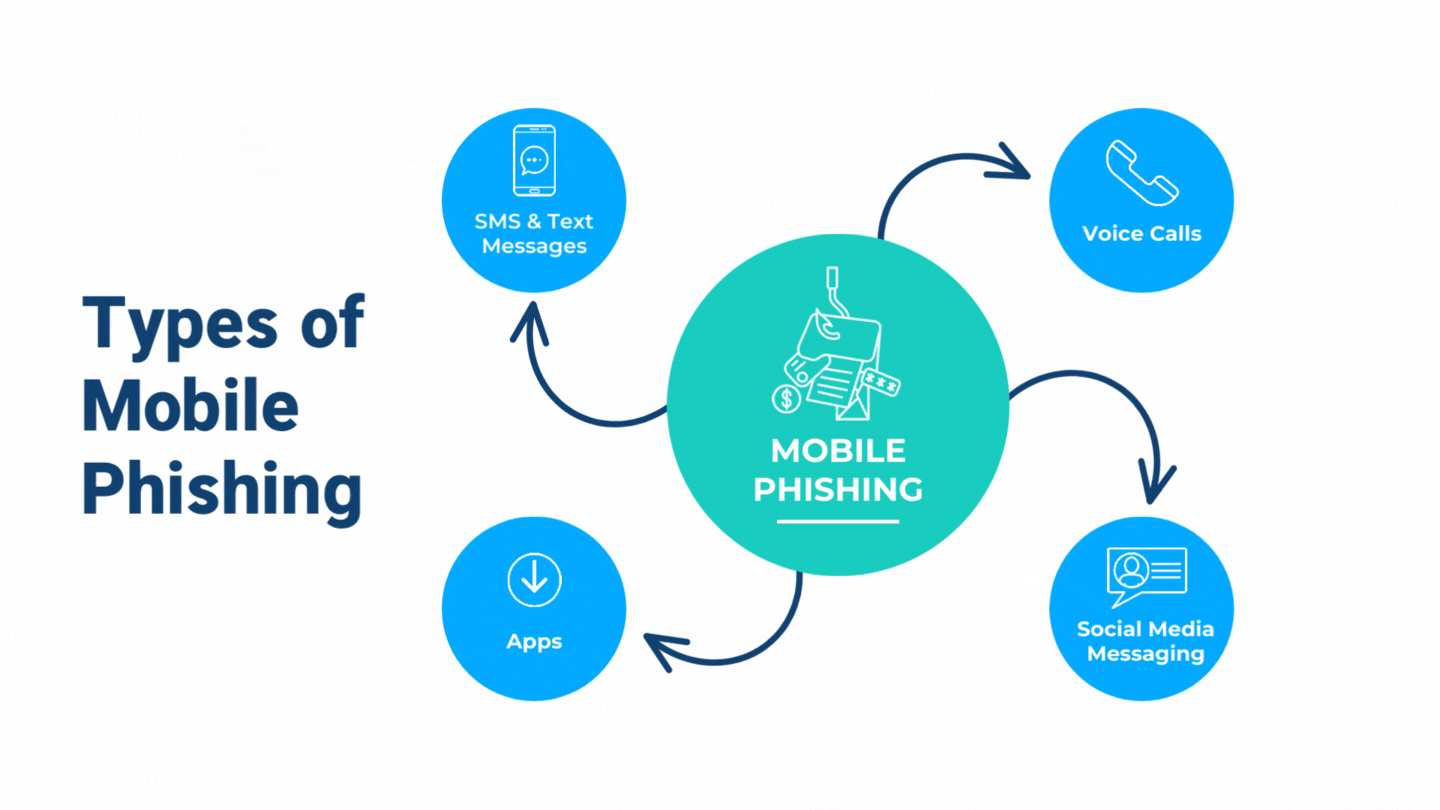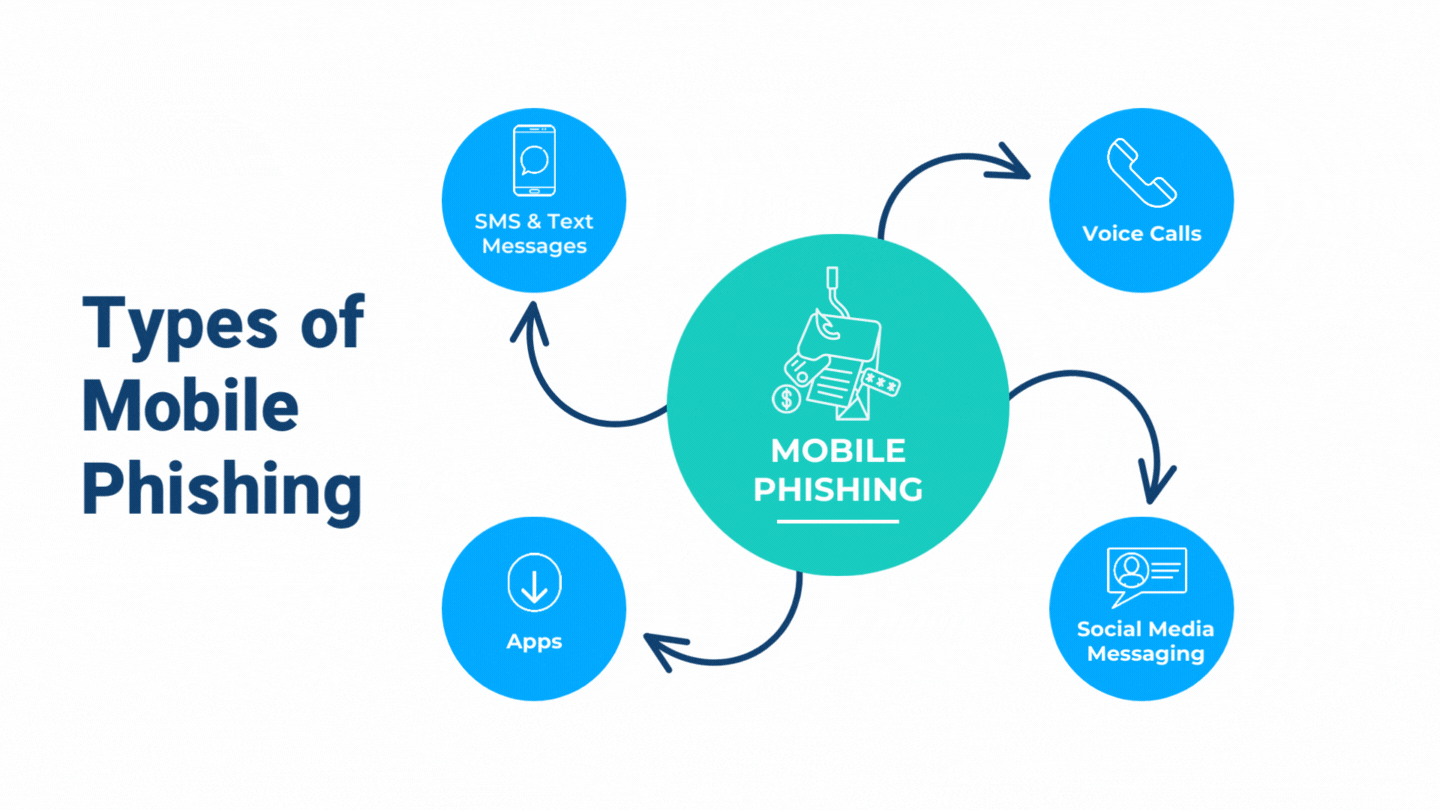
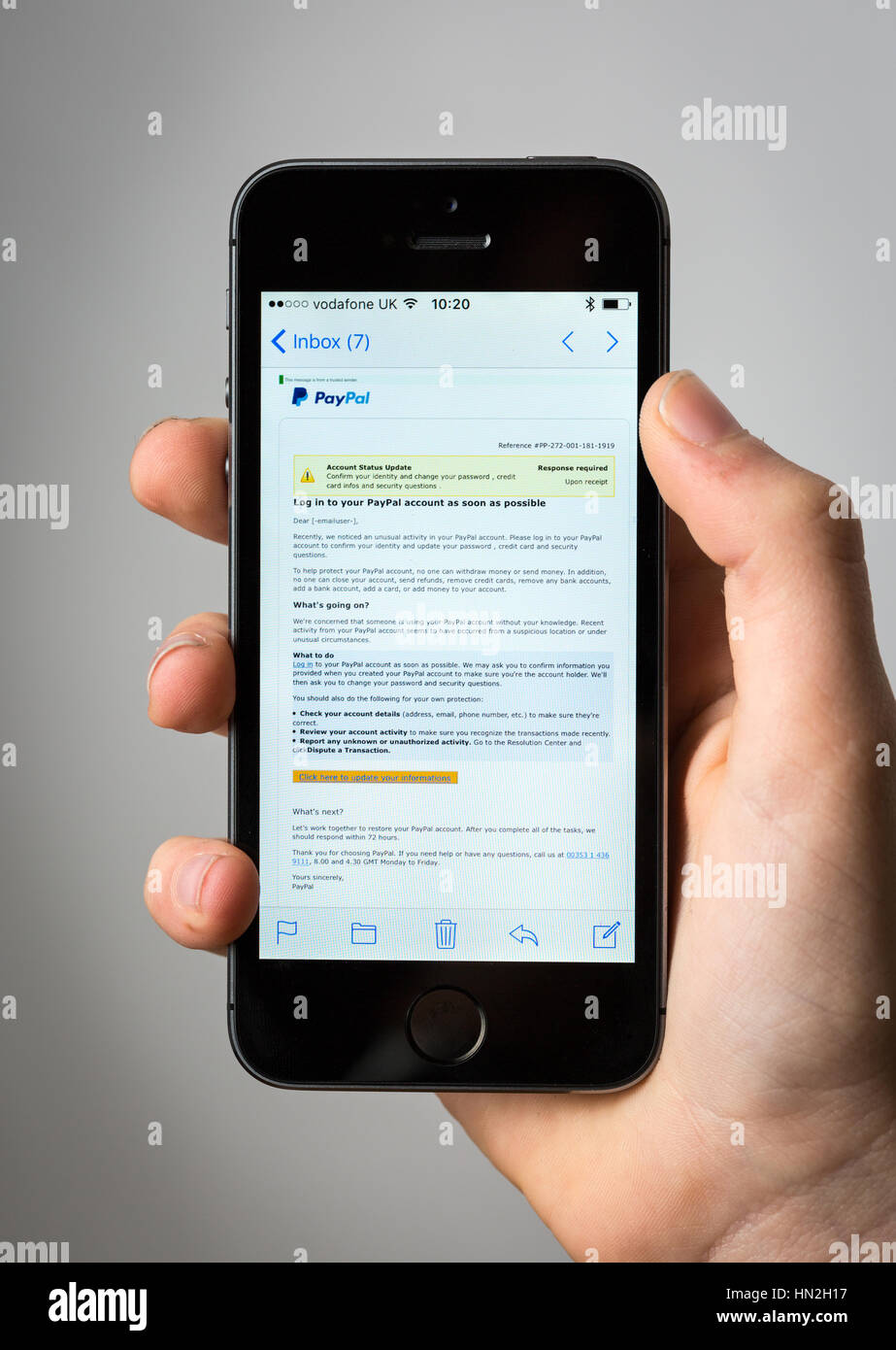
Beware of Phishing Scams Left in Voicemails - Global Tech Solutions Blog | Nationwide Support | Global Tech Solutions

Mobile Phishing Concept - A Fish Hook On A Smart Phone Stock Photo, Picture And Royalty Free Image. Image 32228228.

Mobile Phishing Concept - A Fish Hook On A Smart Phone Stock Photo, Picture And Royalty Free Image. Image 32228232.