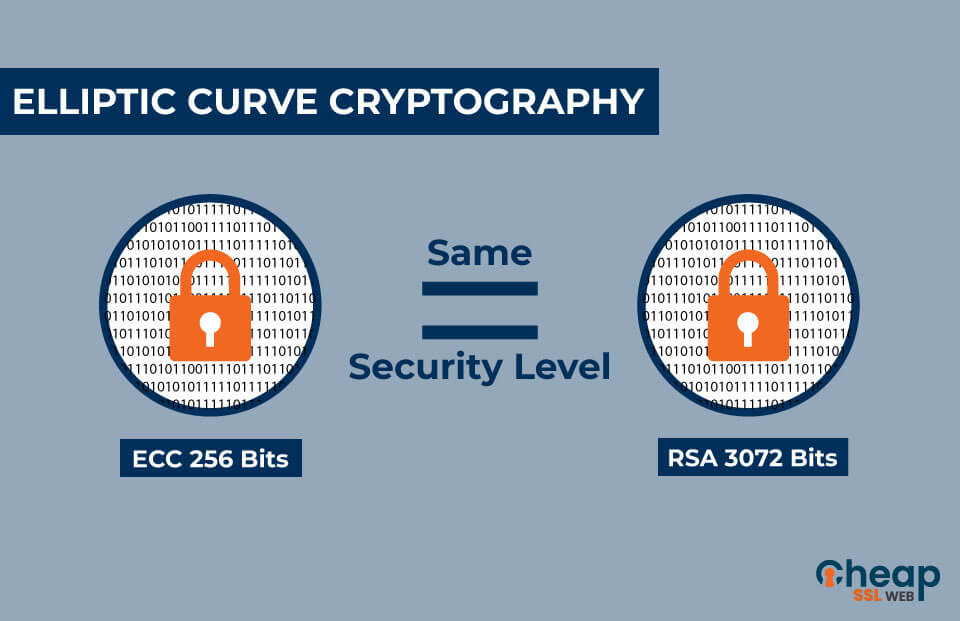
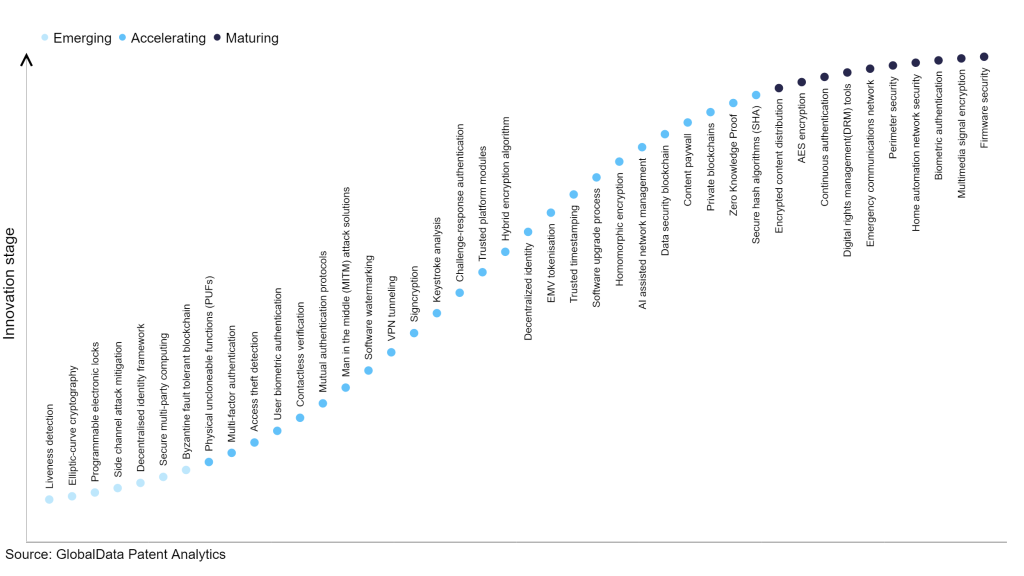
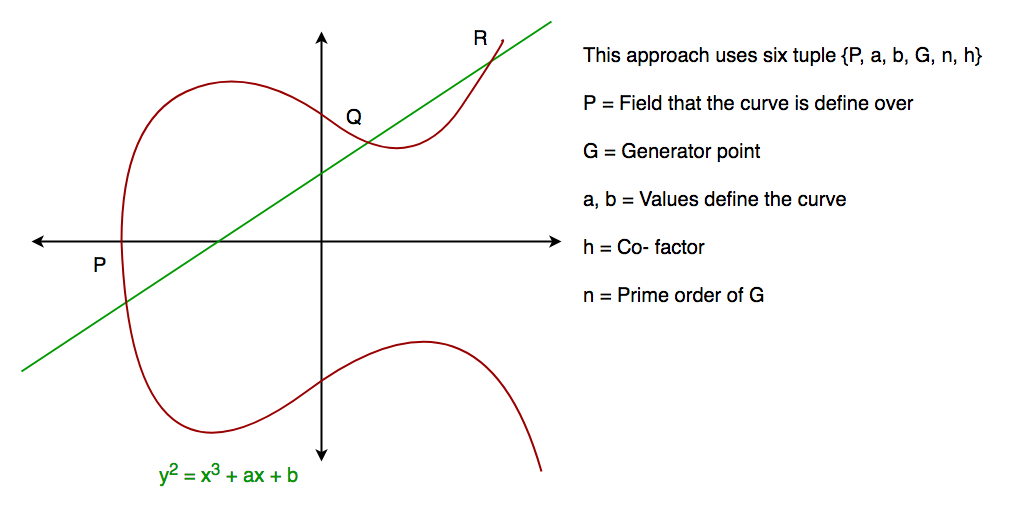
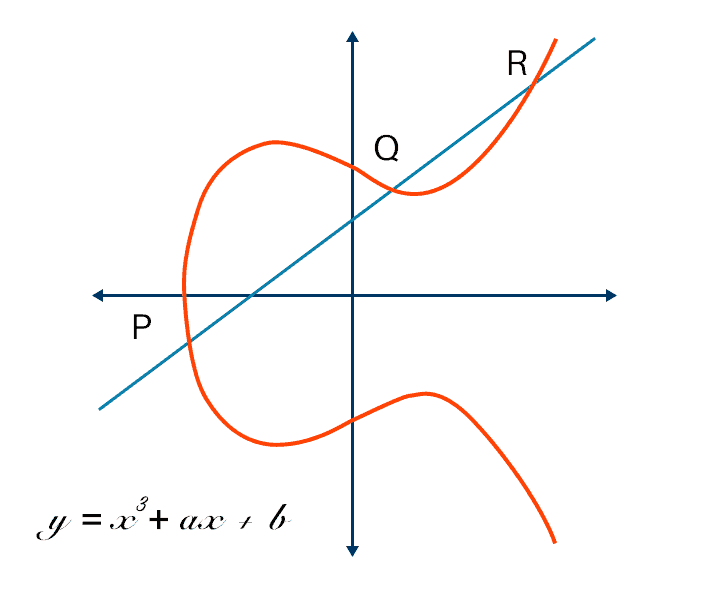Ensure that the best encryption practices are implemented for your organization with Elliptic Curve Cryptography | Encryption Consulting
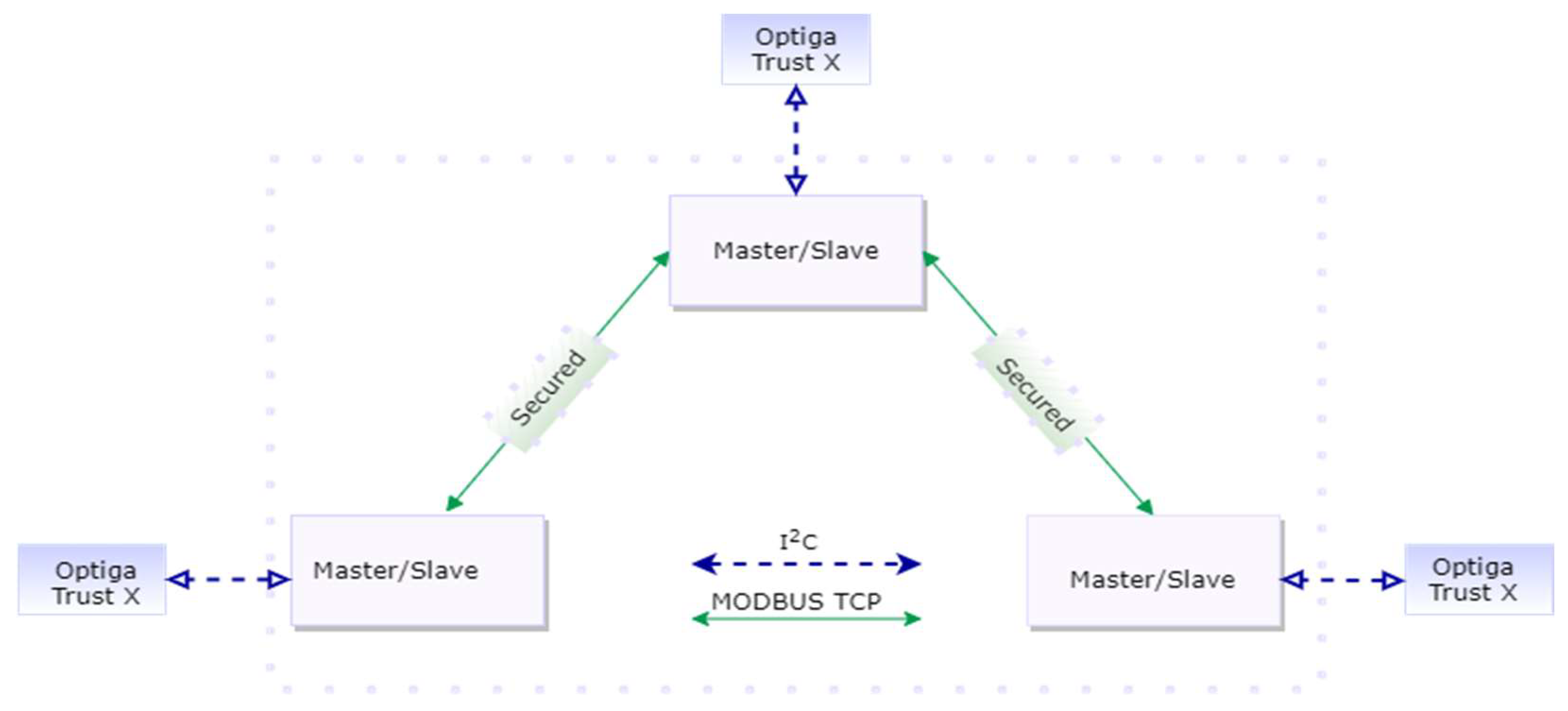
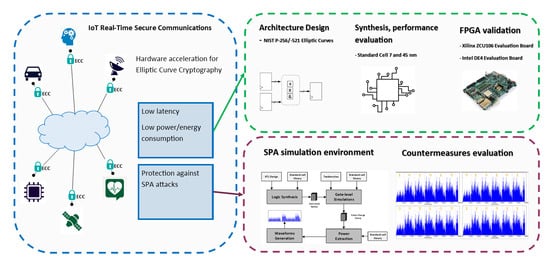
Sensors | Free Full-Text | Elliptic Curve Cryptography Considerations for Securing Automation and SCADA Systems